By Brian Krebs, Security Researcher
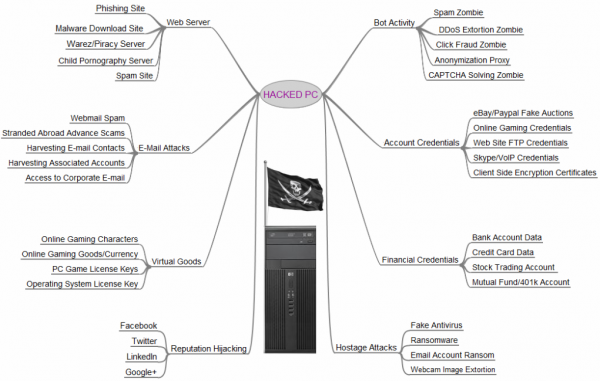
A few years back, when I was a reporter at The Washington Post, I put together a chart listing the various ways that miscreants can monetize hacked PCs. The project was designed to explain simply and visually to the sort of computer user who can’t begin to fathom why miscreants would want to hack into his PC. “I don’t bank online, I don’t store sensitive information on my machine! I only use it to check email. What could hackers possibly want with this hunk of junk?,” are all common refrains from this type of user.
I recently updated the graphic (below) to include some of the increasingly prevalent malicious uses for hacked PCs, including hostage attacks — such as ransomware — and reputation hijacking on social networking forums.
One of the ideas I tried to get across with this image is that nearly every aspect of a hacked computer and a user’s online life can be and has been commoditized. If it has value and can be resold, you can be sure there is a service or product offered in the cybercriminal underground to monetize it. I haven’t yet found an exception to this rule.
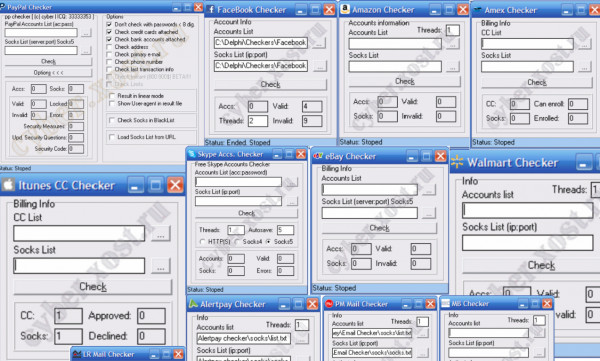
By way of example, consider the point-and-click tools pictured below, which are offered on several fraud forums by one enterprising young miscreant. This guy makes and markets dozens of account checking tools that are used to test the validity and status of many popular online stores and services, including Amazon, American Express, eBay, Facebook, iTunes, PayPal and Skype, to name a few.
Principally, I see the hacked PC graphic as a way to capture the average user’s attention and imagination. Hopefully, these folks can then be guided toward some simple steps to keeping their machine from getting hacked. I’m building a running list of applications, simple tools and tips that can help on this front, available here.